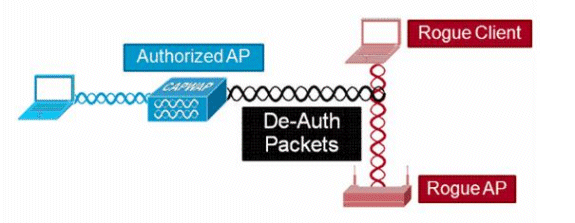
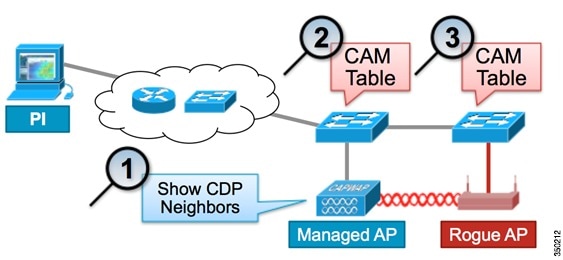
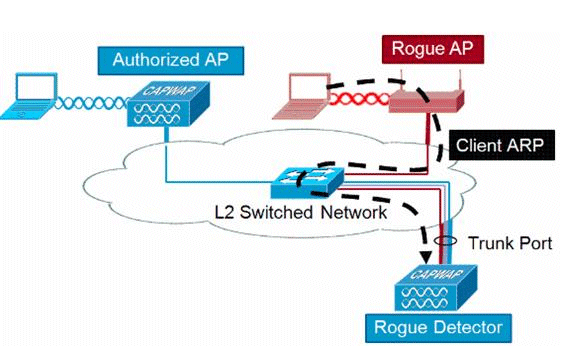
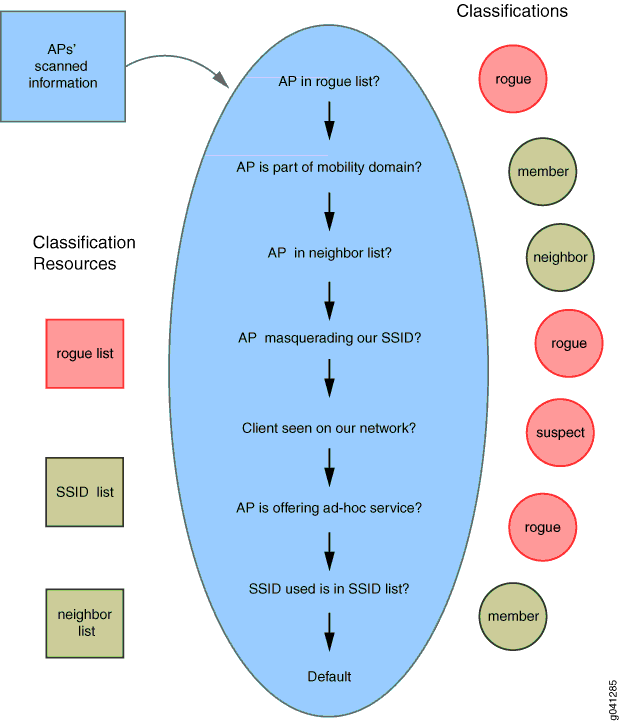
Linksys Official Support - How to enable Rogue AP Detection on your Linksys Wireless-AC Access Point
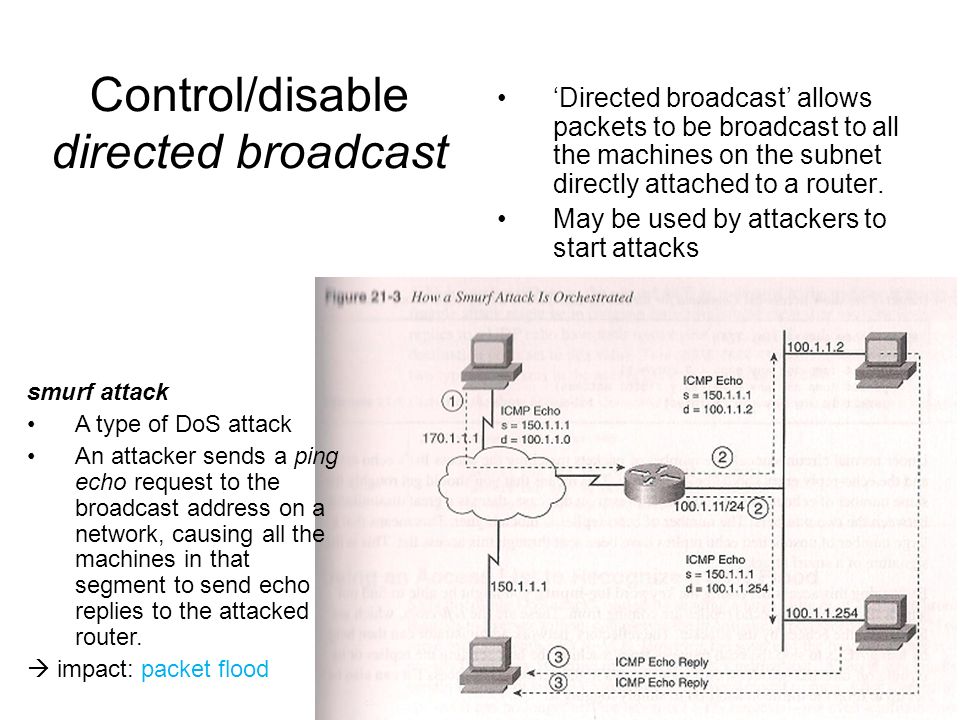
Network Security1 Secure Routing Source: Ch. 4 of Malik. Network Security Principles and Practices (CCIE Professional Development). Pearson Education. - ppt download
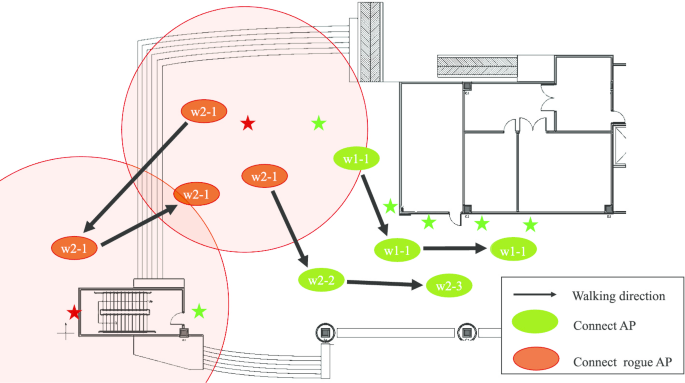
Client-side rogue access-point detection using a simple walking strategy and round-trip time analysis | EURASIP Journal on Wireless Communications and Networking | Full Text

Linksys Official Support - How to enable Rogue AP Detection on your Linksys Wireless-AC Access Point
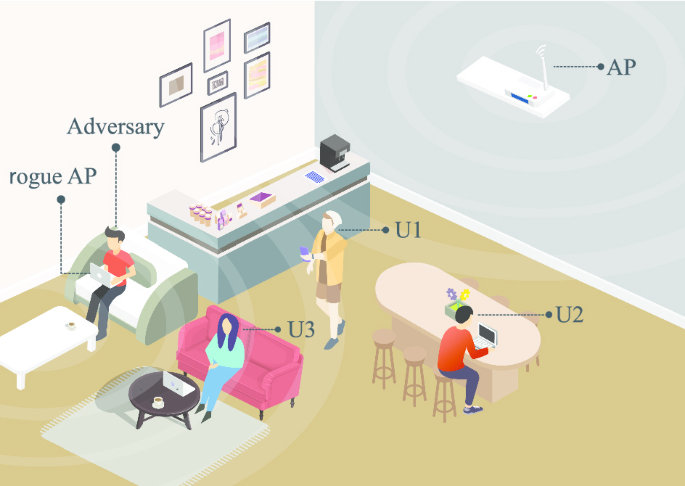
Client-side rogue access-point detection using a simple walking strategy and round-trip time analysis | EURASIP Journal on Wireless Communications and Networking | Full Text