![PDF] Design and performance analysis of a reconfigurable, unified HMAC-hash unit for IPSec authentication | Semantic Scholar PDF] Design and performance analysis of a reconfigurable, unified HMAC-hash unit for IPSec authentication | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/29e3d14005c1eaa694beb29cf1b02bc867317317/31-Figure2.1-1.png)
PDF] Design and performance analysis of a reconfigurable, unified HMAC-hash unit for IPSec authentication | Semantic Scholar
![PDF] Design and performance analysis of a reconfigurable, unified HMAC-hash unit for IPSec authentication | Semantic Scholar PDF] Design and performance analysis of a reconfigurable, unified HMAC-hash unit for IPSec authentication | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/29e3d14005c1eaa694beb29cf1b02bc867317317/23-Figure1.3-1.png)
PDF] Design and performance analysis of a reconfigurable, unified HMAC-hash unit for IPSec authentication | Semantic Scholar

Hash Tables Implementation in Go. The inner implementation. A story (for… | by Marwan Abdel Moneim | kalamsilicon | Medium
![PDF] Design and performance analysis of a reconfigurable, unified HMAC-hash unit for IPSec authentication | Semantic Scholar PDF] Design and performance analysis of a reconfigurable, unified HMAC-hash unit for IPSec authentication | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/29e3d14005c1eaa694beb29cf1b02bc867317317/57-Table3.1-1.png)
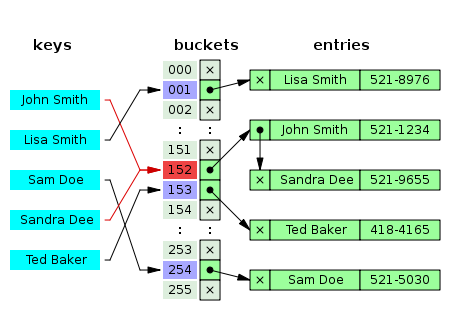



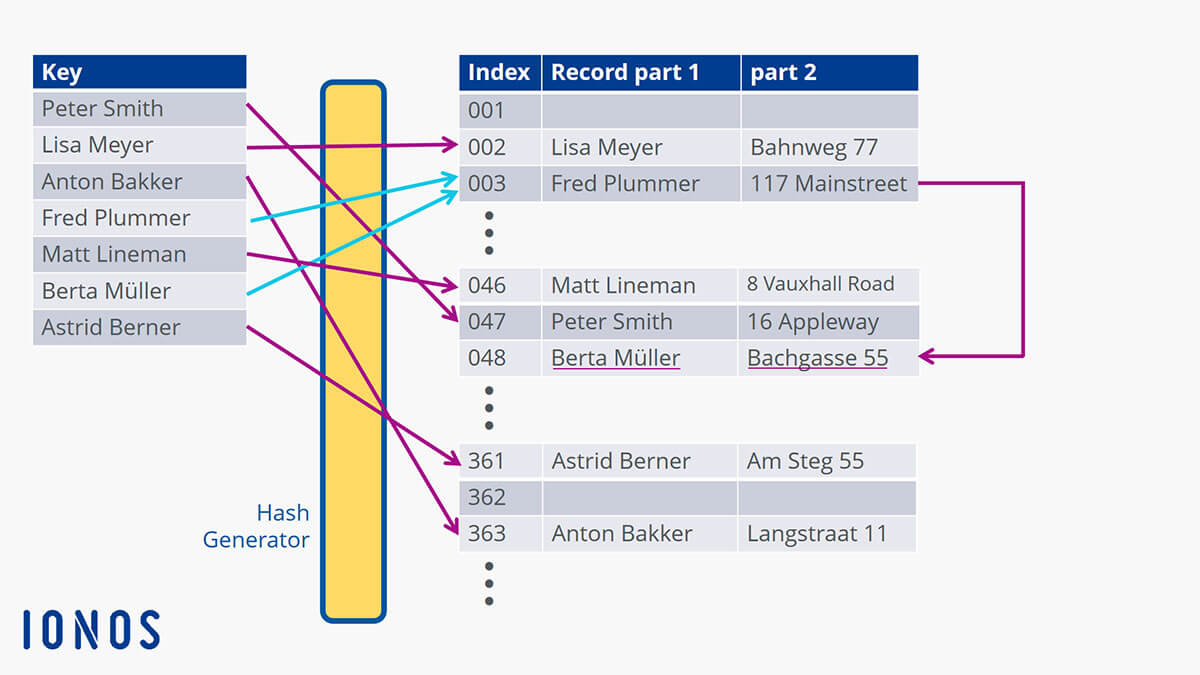



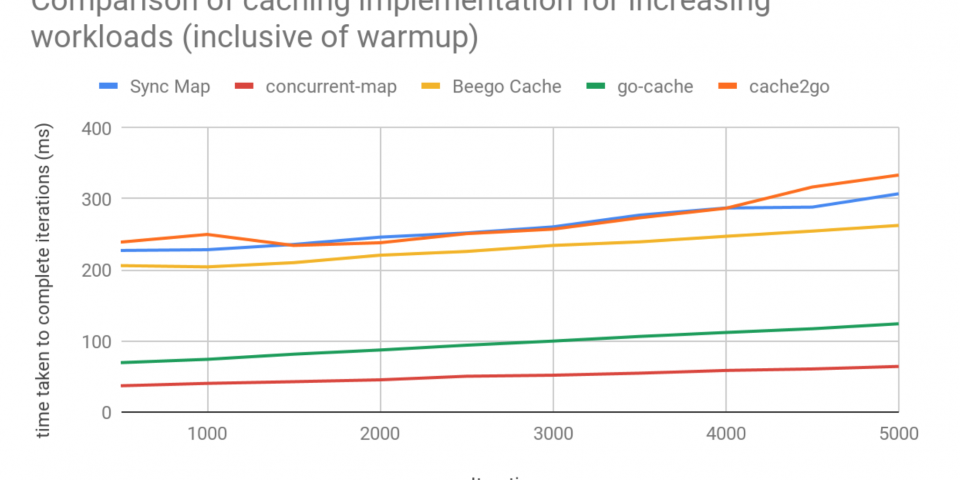

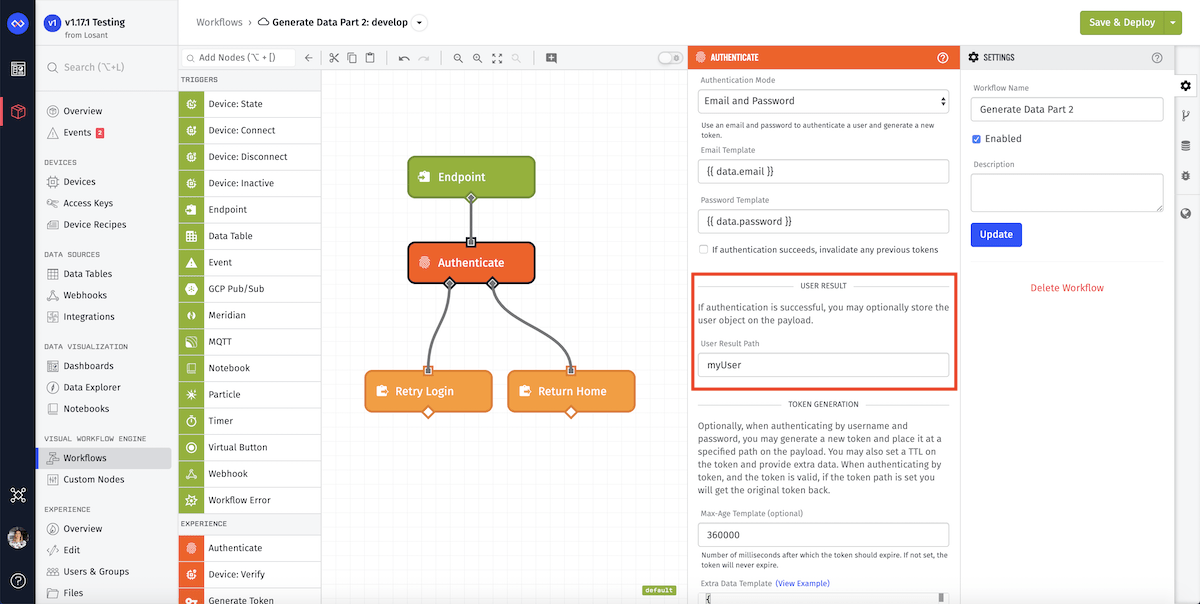
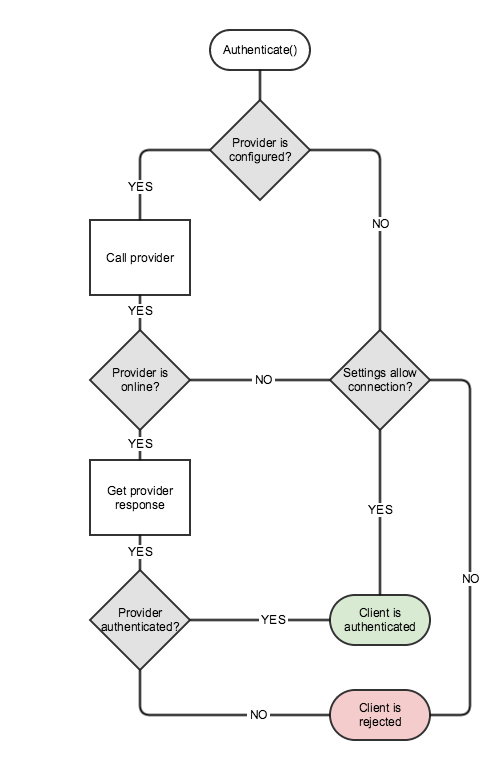




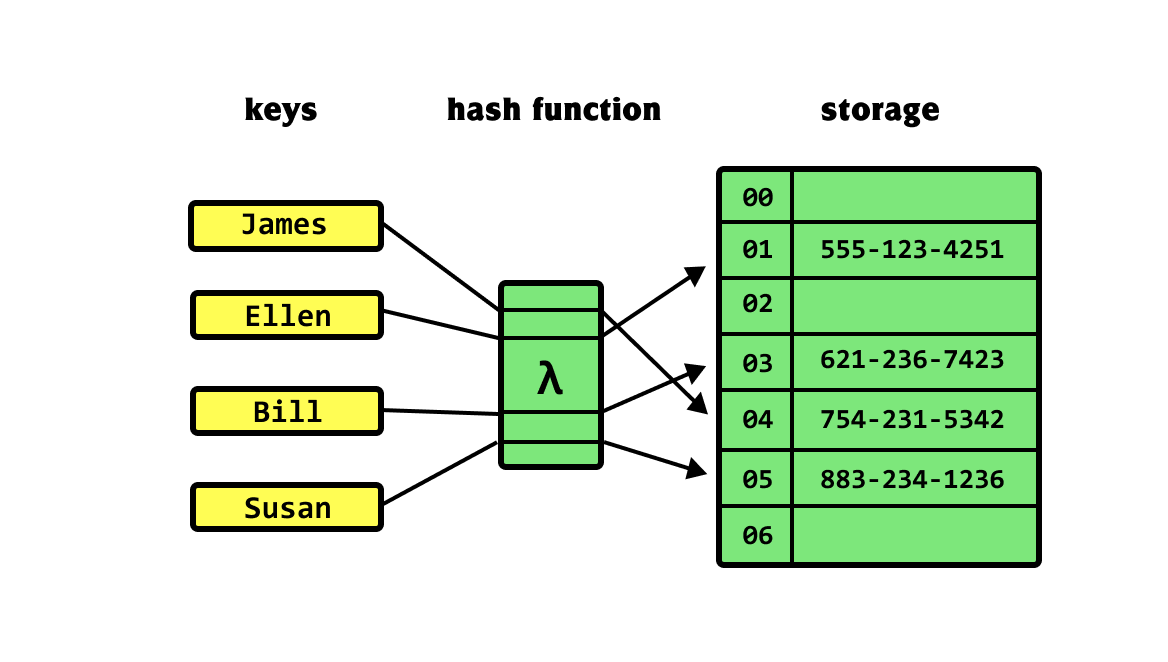
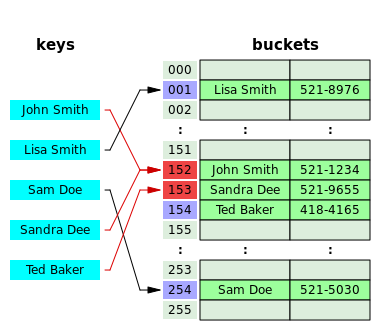
![Hash tables explained [step-by-step example] · YourBasic Hash tables explained [step-by-step example] · YourBasic](https://yourbasic.org/algorithms/hash-table.png)