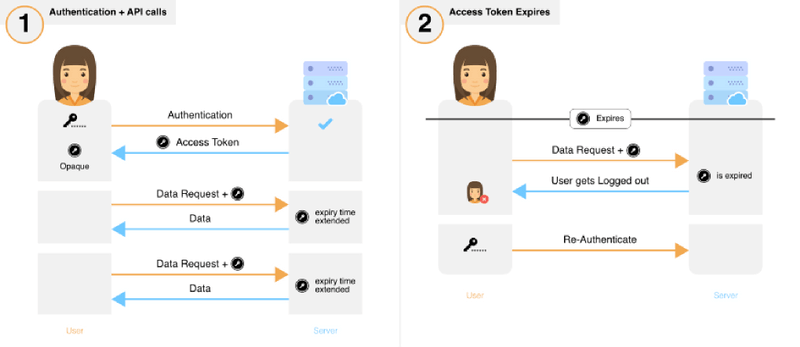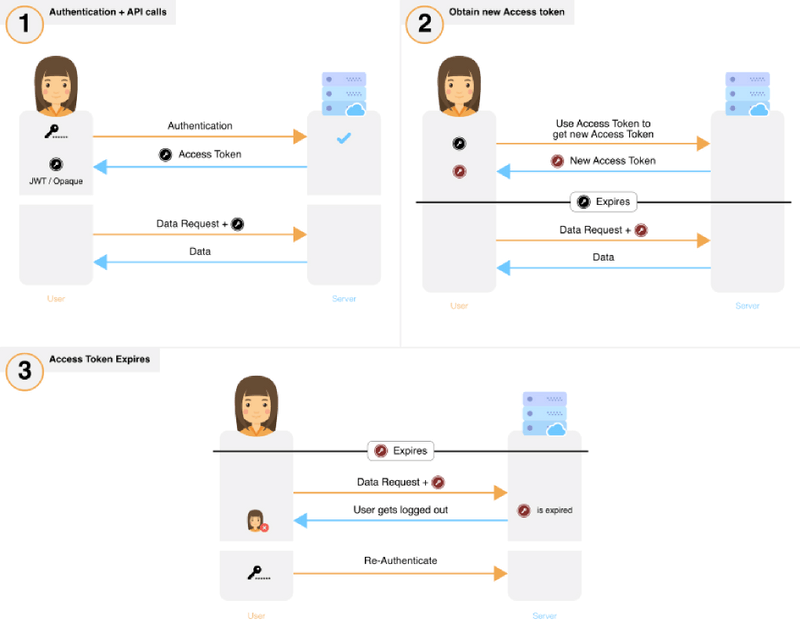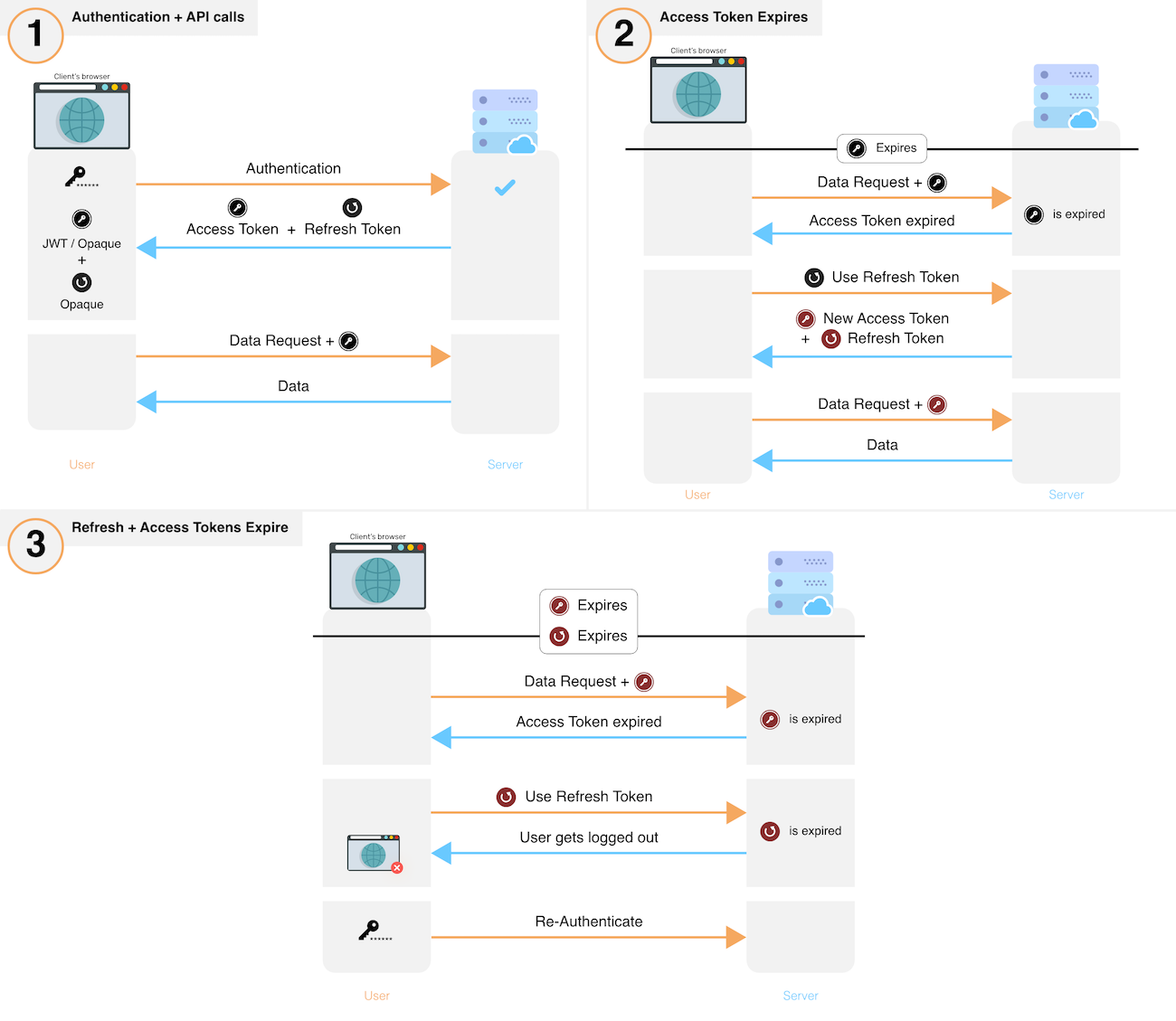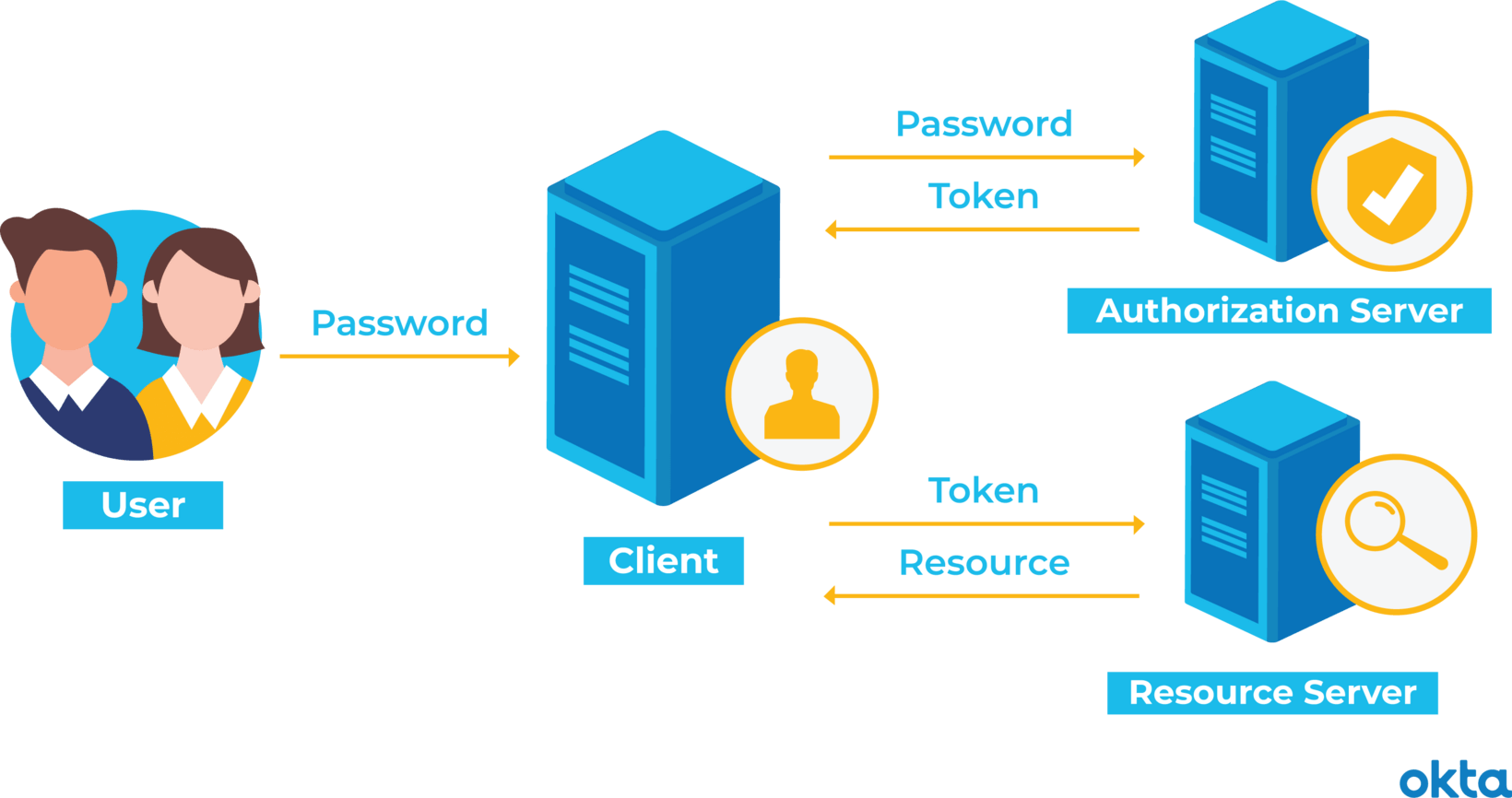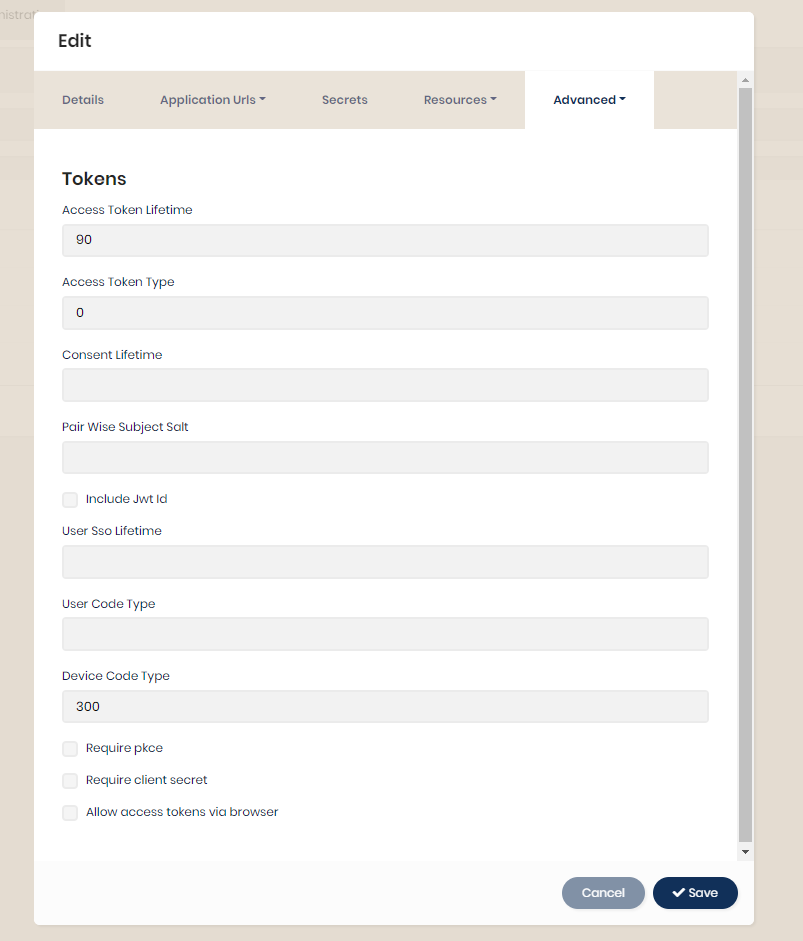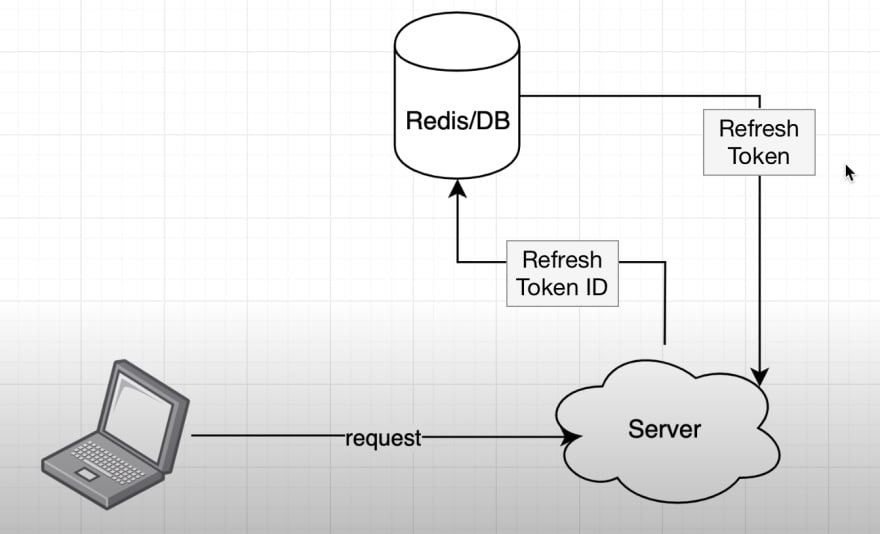
JSON web tokens are NOT meant for authenticating the same user repeatedly: Use session tokens instead - DEV Community 👩💻👨💻
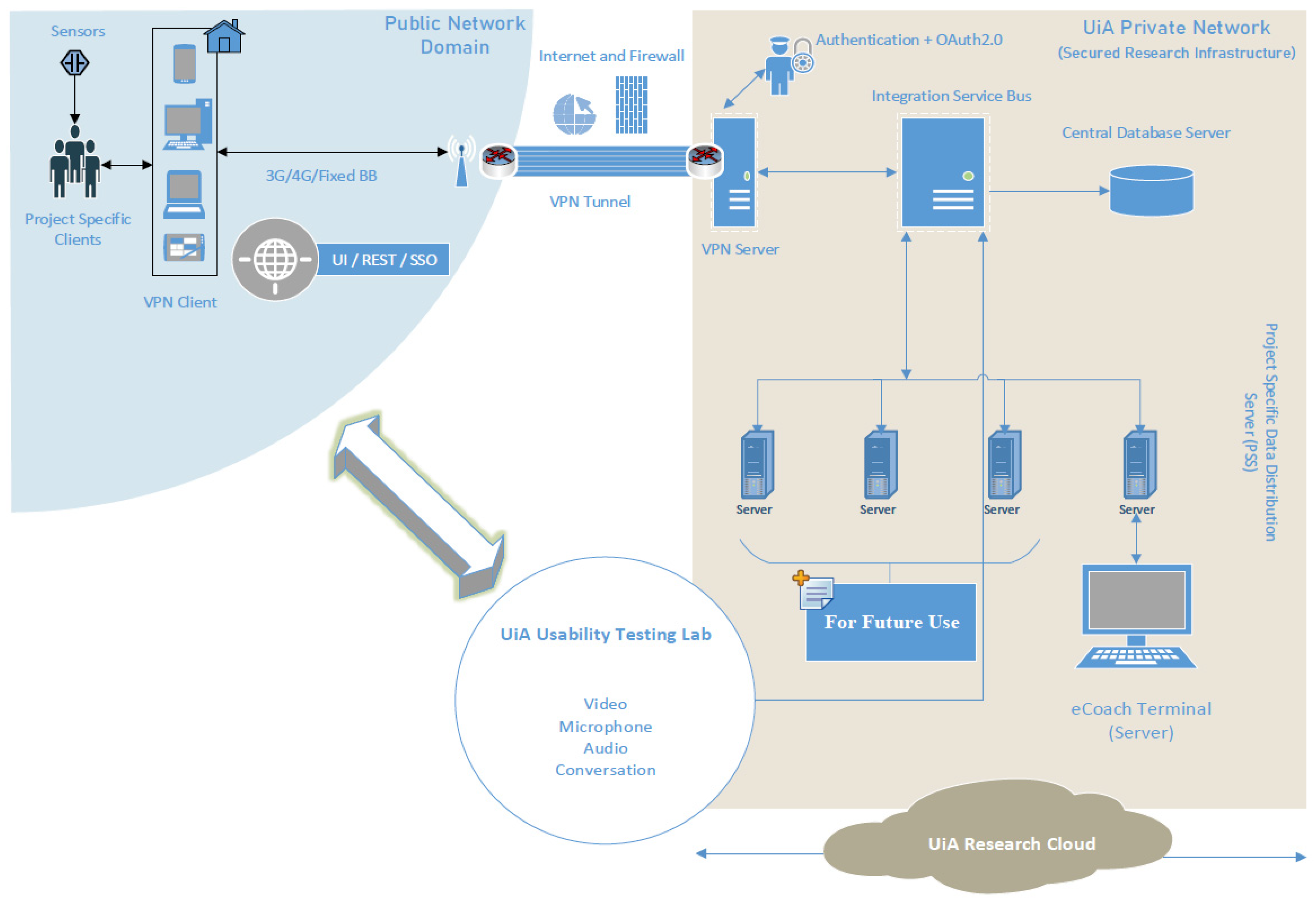
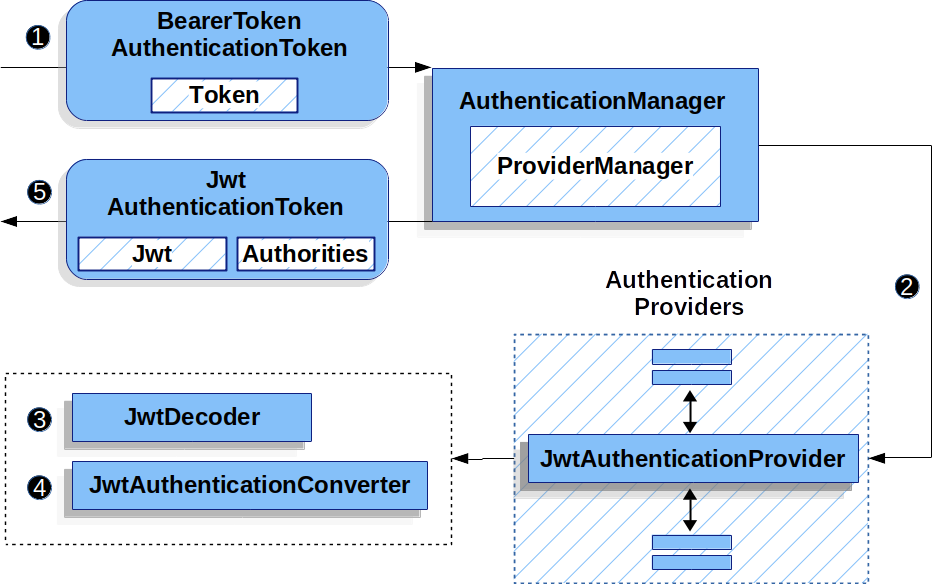
Sensors | Free Full-Text | Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study | HTML