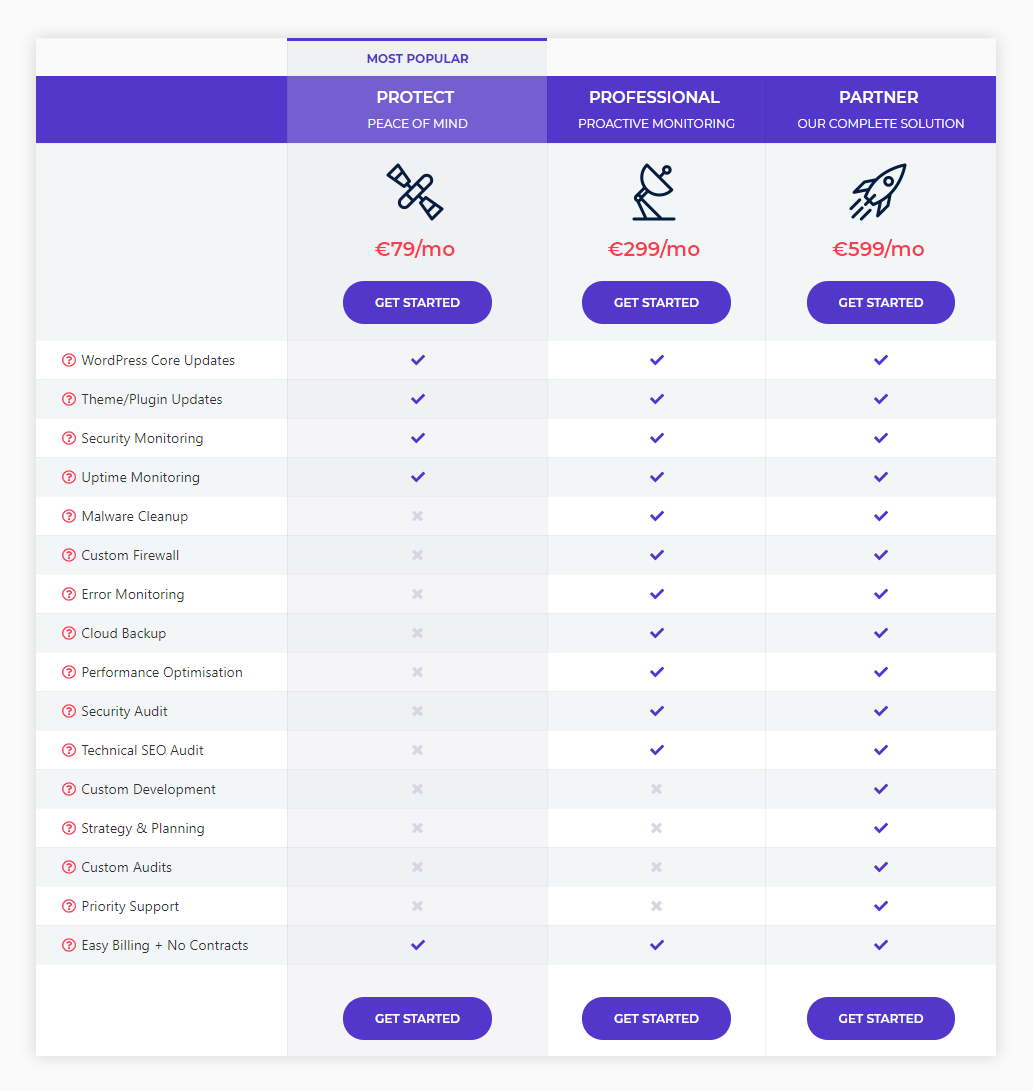
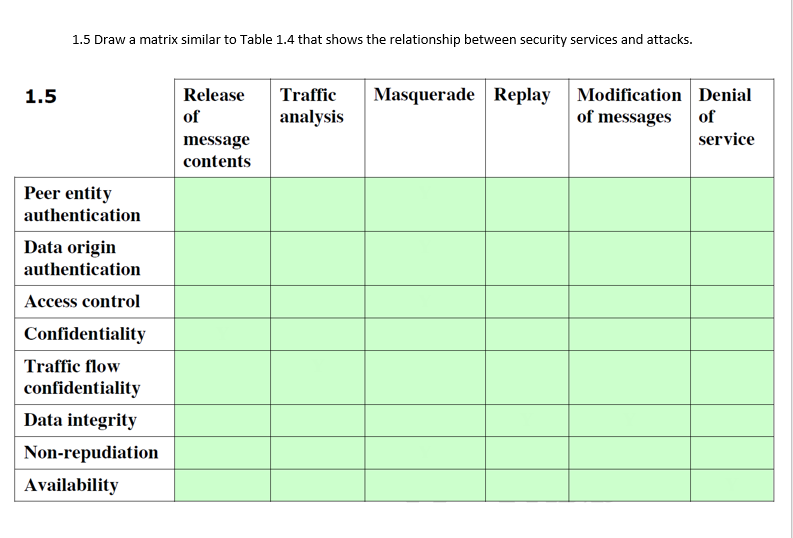
Considerations on Visible Light Communication security by applying the Risk Matrix methodology for risk assessment | PLOS ONE
Skill Matrix Table Identifying Technical Security And Transaction Processing | PowerPoint Slides Diagrams | Themes for PPT | Presentations Graphic Ideas

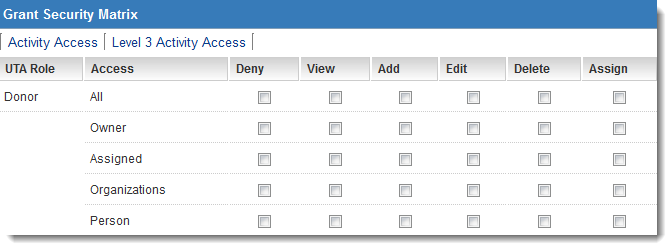
To improve the current security model and efficiency in cloud computing using access control matrix | Semantic Scholar
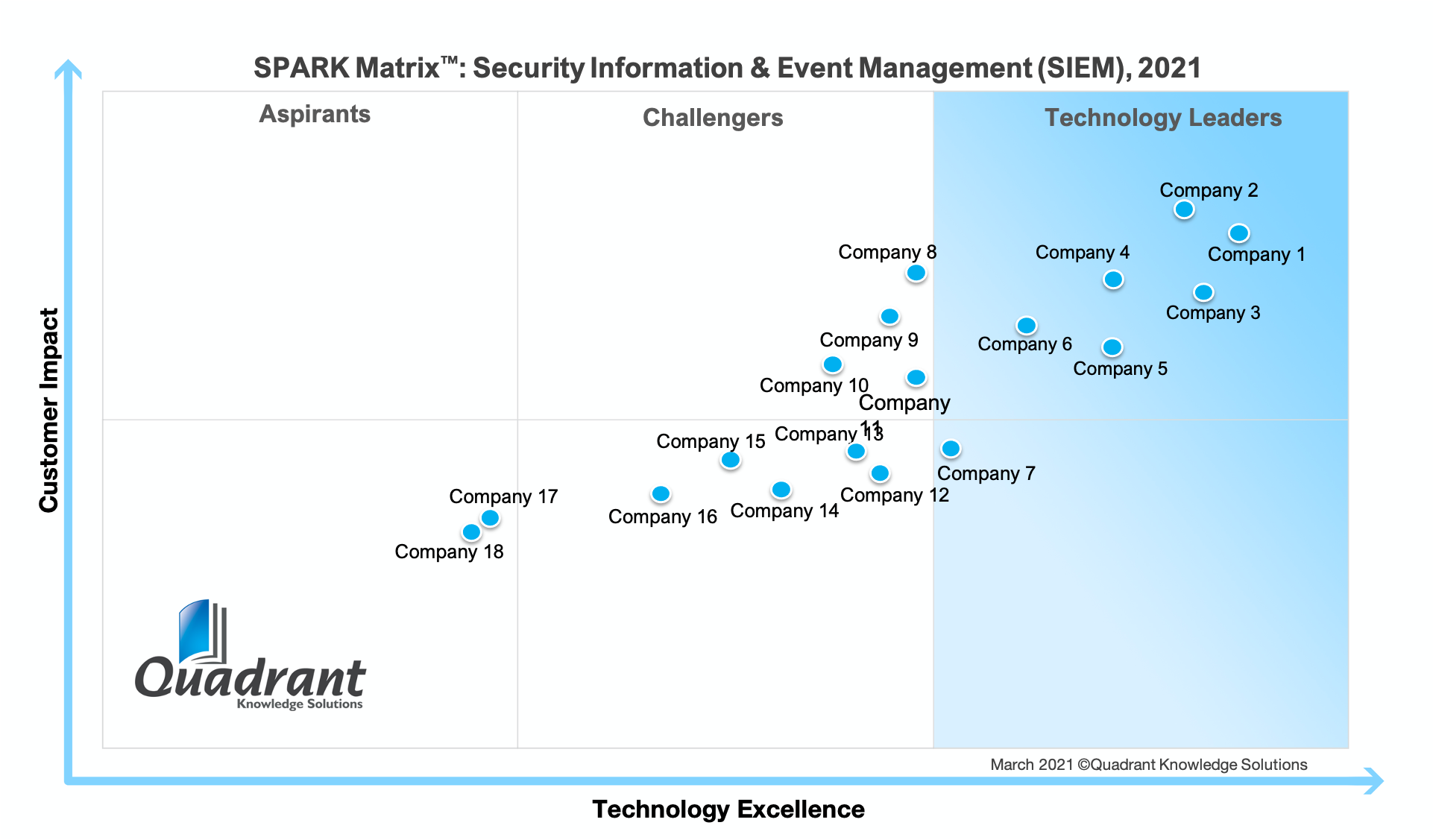
SPARK Matrix™: Security Information and Event Management (SIEM), 2021 - Quadrant Knowledge Solutions SPARK Matrix™: Security Information and Event Management (SIEM), 2021

Matrix of the Internet Security Framework. The table shows security... | Download Scientific Diagram