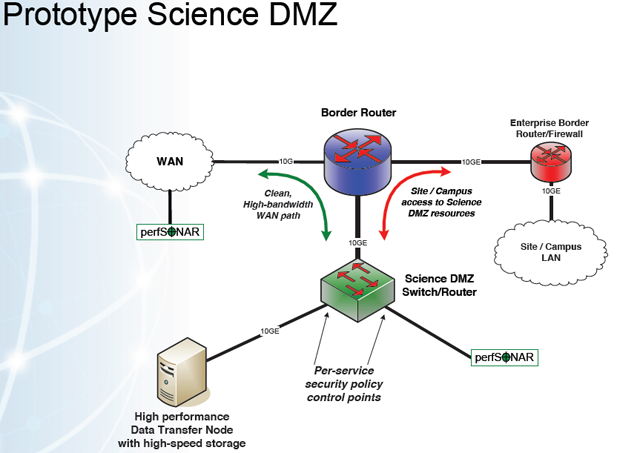
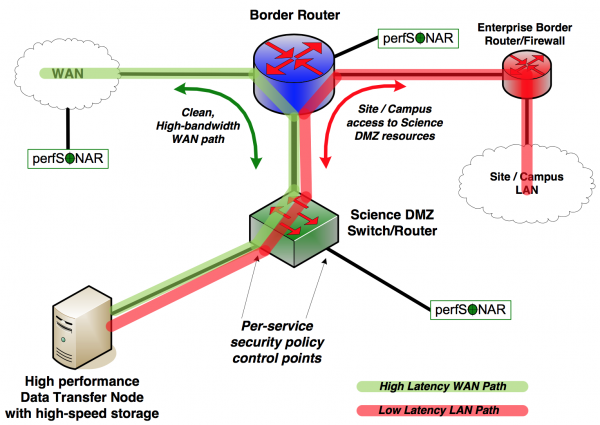
Switch Security: Management and Implementation (2.2) > Cisco Networking Academy's Introduction to Basic Switching Concepts and Configuration | Cisco Press
![Networking and Security in Industrial Automation Environments Design and Implementation Guide - Networking and Security in Industrial Automation Environments [Network Security] - Cisco Networking and Security in Industrial Automation Environments Design and Implementation Guide - Networking and Security in Industrial Automation Environments [Network Security] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/370001-380000/379001-380000/379403.jpg)
Networking and Security in Industrial Automation Environments Design and Implementation Guide - Networking and Security in Industrial Automation Environments [Network Security] - Cisco

Switch Security: Management and Implementation (2.2) > Cisco Networking Academy's Introduction to Basic Switching Concepts and Configuration | Cisco Press


/Router-vs-Switch-5783607be8cb433e8b6feb68c356866c.jpg)
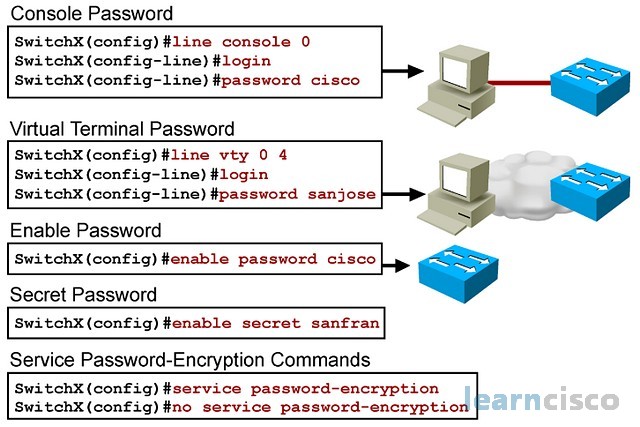







![4. VLANs and Trunking - Packet Guide to Routing and Switching [Book] 4. VLANs and Trunking - Packet Guide to Routing and Switching [Book]](https://www.oreilly.com/api/v2/epubs/9781449311315/files/assets/pgrs_0401.png)