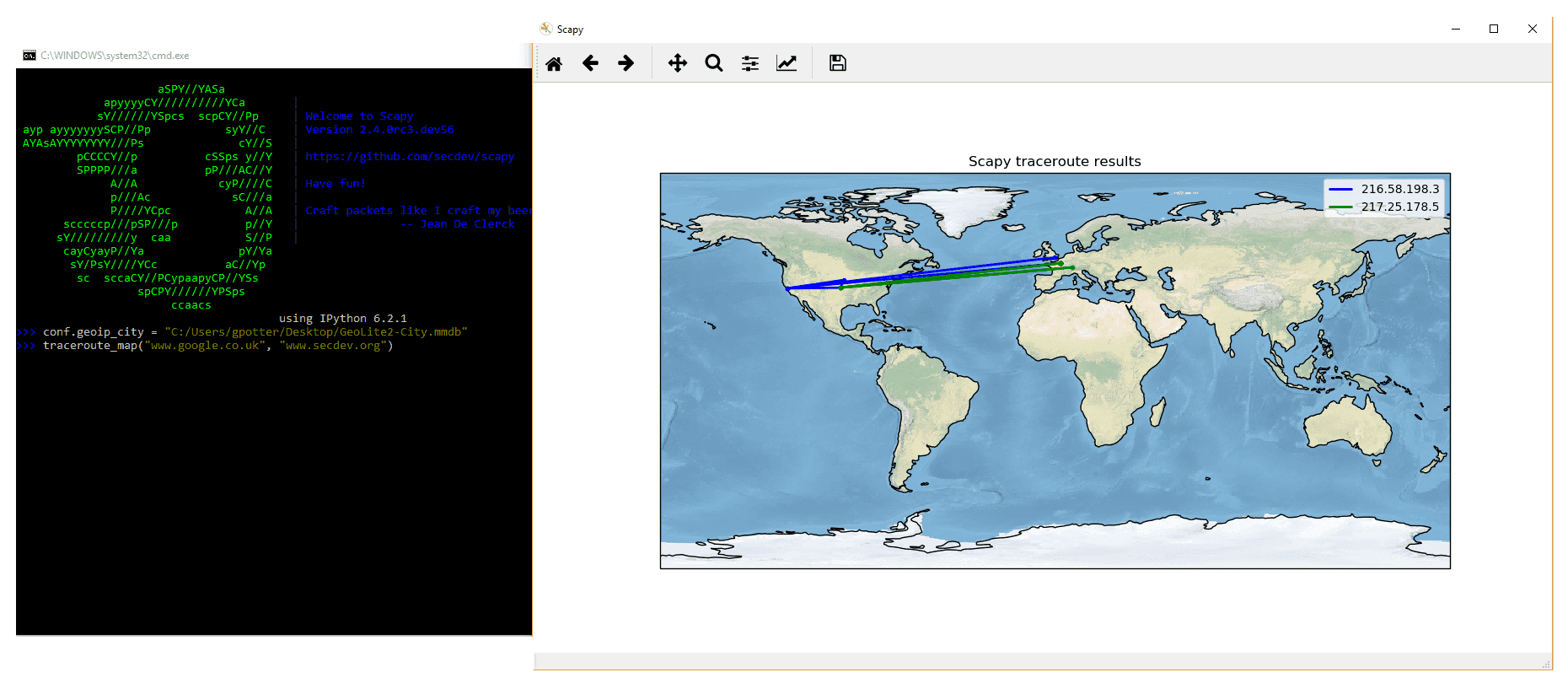
Smuggler and Cove: A PoC for data exfiltration using Scapy. | by Sean Greathouse | The Startup | Medium

Man‐in‐the‐middle attacks and defence in a power system cyber‐physical testbed - Wlazlo - 2021 - IET Cyber-Physical Systems: Theory & Applications - Wiley Online Library


![PDF] Network Web Traffic Generator for Cyber Range Exercises | Semantic Scholar PDF] Network Web Traffic Generator for Cyber Range Exercises | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/53b4a510840adb05381f36b47db969016f57332b/1-Figure1-1.png)

![PDF] Network Web Traffic Generator for Cyber Range Exercises | Semantic Scholar PDF] Network Web Traffic Generator for Cyber Range Exercises | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/53b4a510840adb05381f36b47db969016f57332b/8-Figure9-1.png)
![PDF] Network Web Traffic Generator for Cyber Range Exercises | Semantic Scholar PDF] Network Web Traffic Generator for Cyber Range Exercises | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/53b4a510840adb05381f36b47db969016f57332b/4-Figure2-1.png)

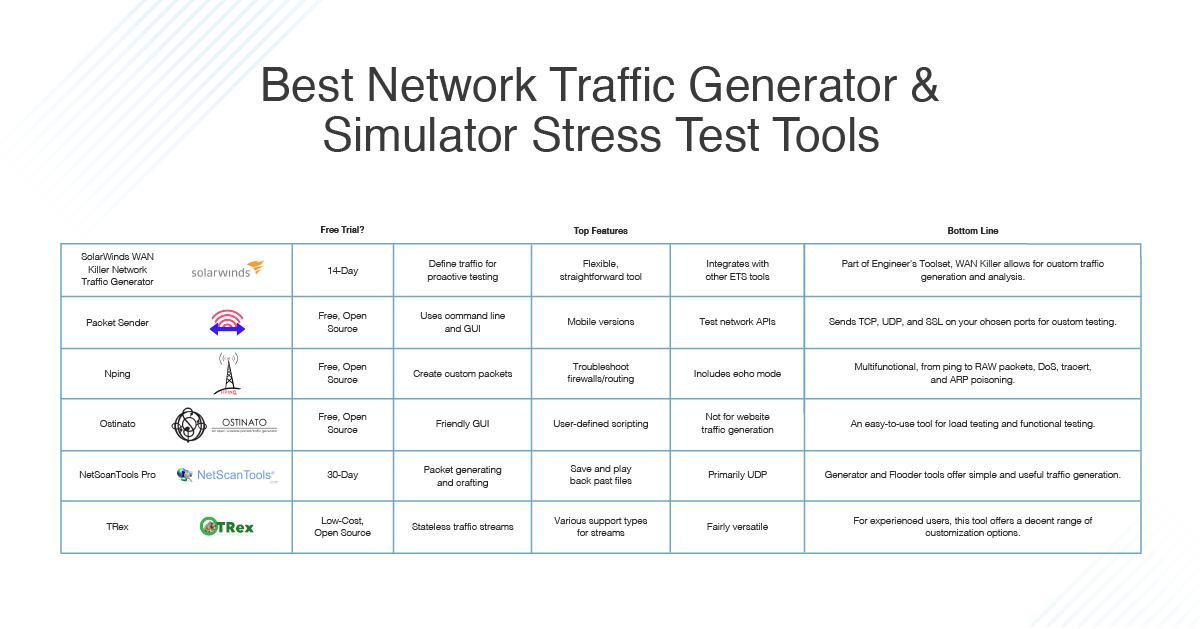




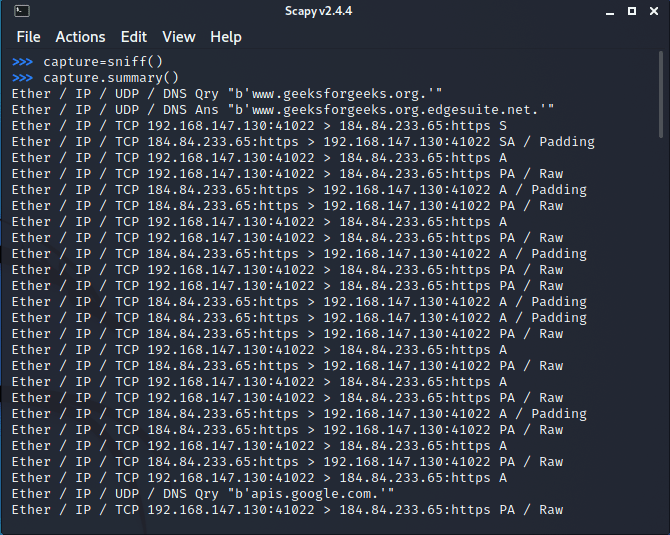
![PDF] Network Web Traffic Generator for Cyber Range Exercises | Semantic Scholar PDF] Network Web Traffic Generator for Cyber Range Exercises | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/53b4a510840adb05381f36b47db969016f57332b/5-Figure4-1.png)

![PDF] Network Web Traffic Generator for Cyber Range Exercises | Semantic Scholar PDF] Network Web Traffic Generator for Cyber Range Exercises | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/53b4a510840adb05381f36b47db969016f57332b/5-Figure3-1.png)