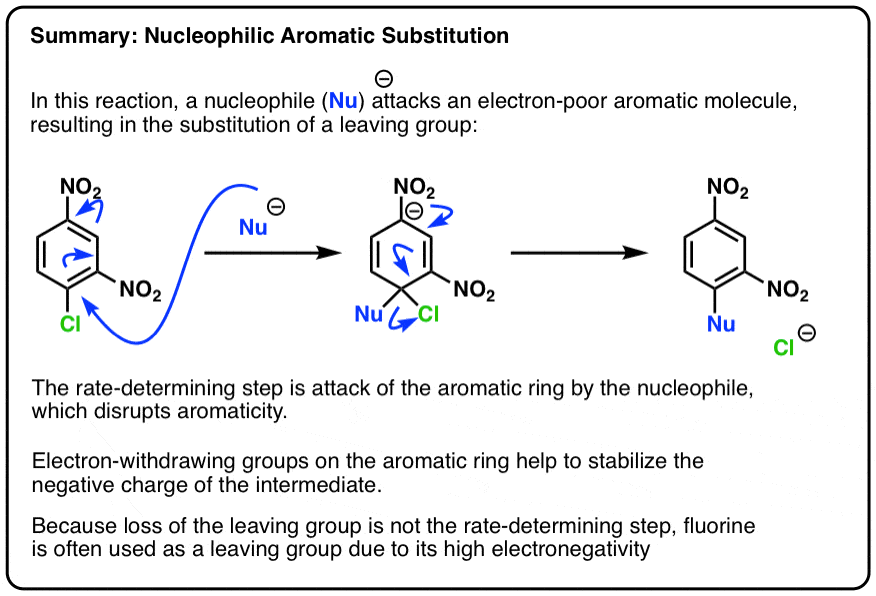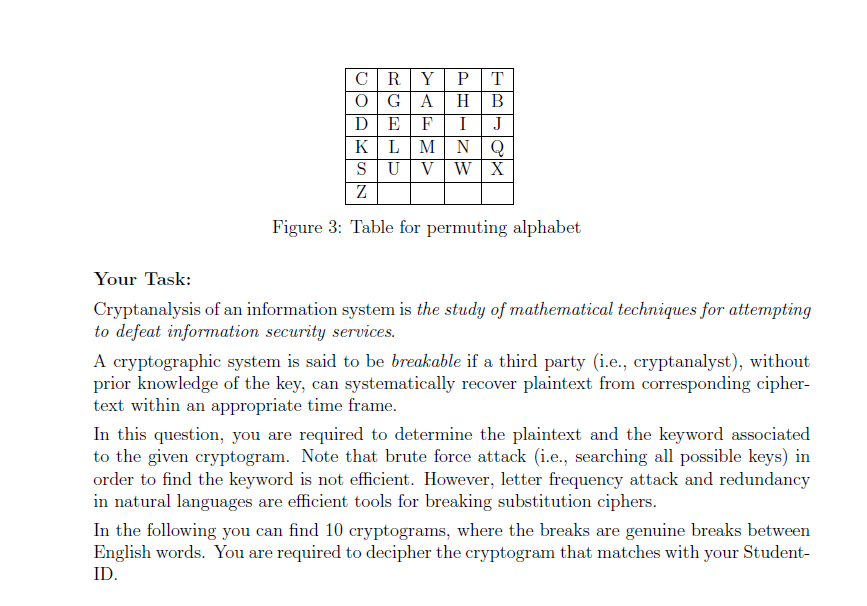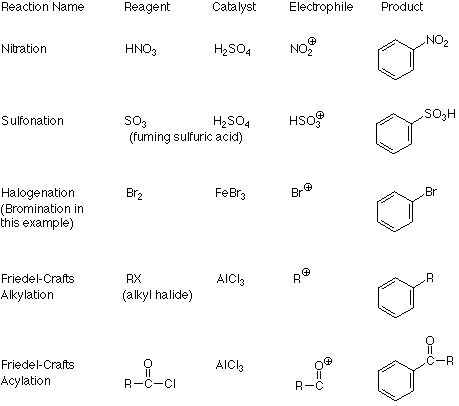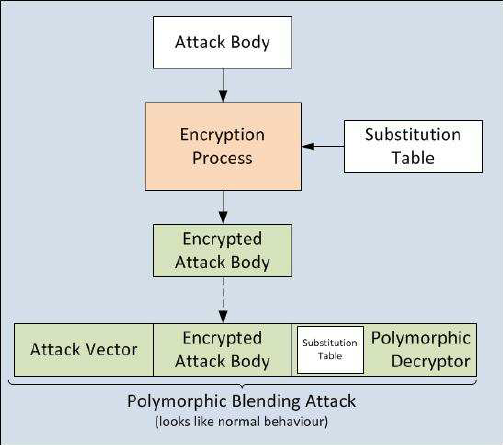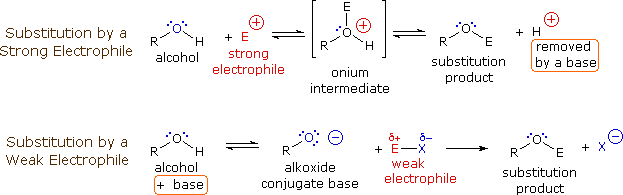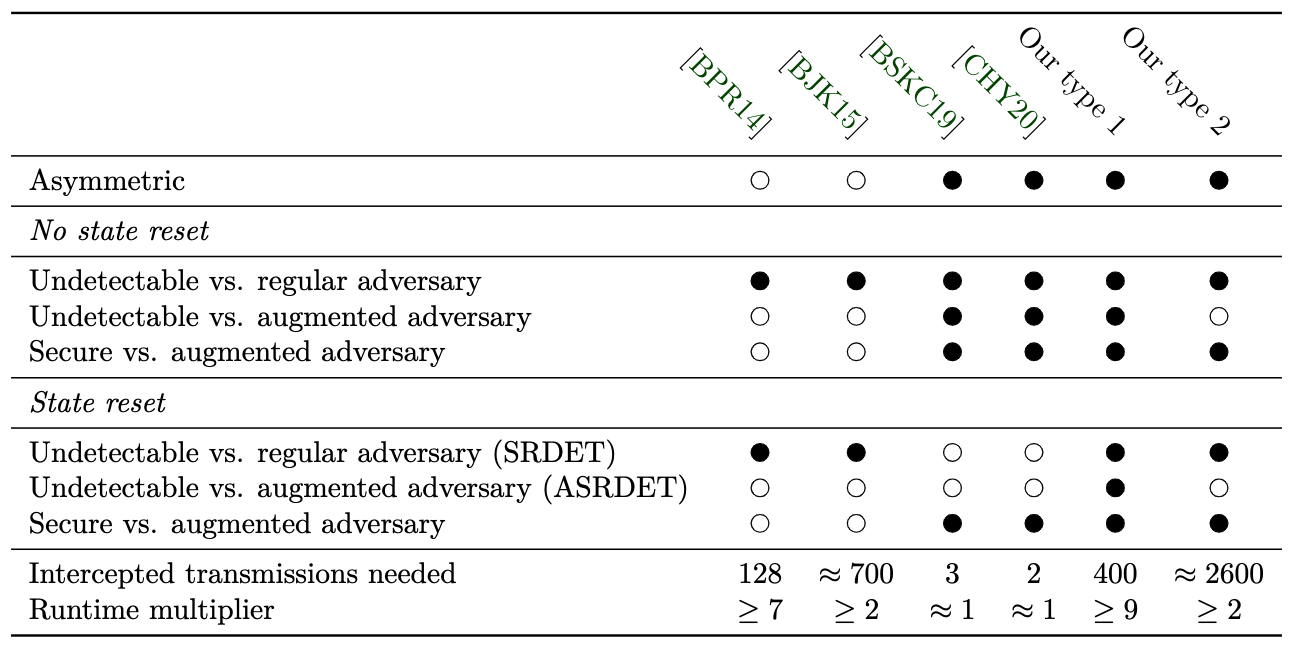
Algorithm substitution attacks: state reset detection and asymmetric modifications • Douglas Stebila
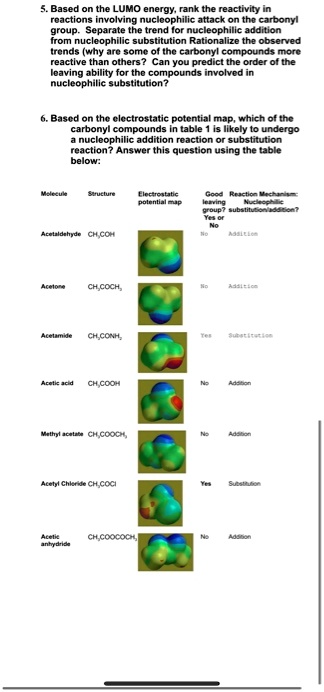
SOLVED: Base the LUMO energy: rank the reactivity roactions invoiving nucleophilic attack on the carbonyl group Separate the trend nucleophilic addmuon Itom nucleophilic substitution Rationalize the observed (rcnot (Wny Arc *omt cardonyi

Stereospecific and stereoconvergent nucleophilic substitution reactions at tertiary carbon centers - ScienceDirect